Public/Private Key Authentication for SFTP
When configuring an SFTP server, you now have the option to use public/private key authentication instead of a username and password to connect to the server. This option requires that you have a private/public SSH key pair, and that the public key is in place on your SFTP server.
On the FTP Properties dialog, when the SFTP protocol is selected you will now see an SFTP Settings area. Check the box if you wish to Use key authentication for this SFTP server.

Click the Read Fingerprint button to request the public key fingerprint from the server. The fingerprint is a hash of the FTP server's public key, which MAPS stores in order to verify that it is connecting to the correct SFTP server.
The option to Always trust server prevents MAPS from verifying that the stored fingerprint matches the fingerprint from the server when using key authentication. You would usually only check this option when connecting to internal servers or testing environments where you are not concerned about man-in-the-middle attacks.
If key authentication is not enabled, you will need to specify a username and password in the section below the SFTP settings as you did previously.
FTP Servers - Keys Screen
Underneath the FTP screen, there is now a Keys screen where you add the private SSH key(s) to MAPS. Keys installed here must correspond to the public key on your SFTP server. When connecting to an SFTP server, MAPS attempts to authenticate to the server using the first key in the list. If authentication fails, it goes down the list of keys until a match is found or until all keys have been tried.
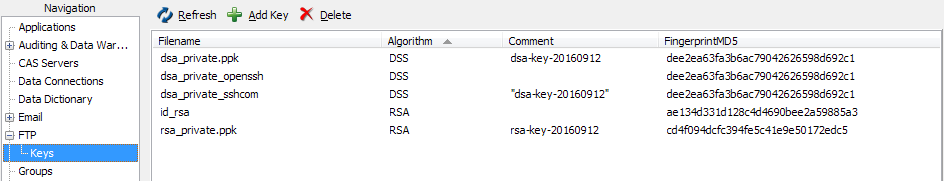
Click Add Key to browse for a key file to import. The key and its details will then be added to the list on the Keys screen.
- Filename - The name of the key file of the private key.
- Algorithm - Specifies the encryption algorithm used for the key. MAPS supports DSA and RSA encryption.
- Comment - The "Comment" field from within the key file.
- Fingerprint (MD5) - The fingerprint (hash) of the key.
Key Format
MAPS supports SSH keys generated using the DSA or RSA encryption algorithms.
You can generate the SSH key pair using a program of your choice. PuTTYgen is a free, open-source utility (not supplied by Evisions) that can be used for this purpose. Please refer to their documentation for installation and usage instructions.
You should store the private key in a secure location, making sure it is not distributed to any other party. Messages encoded using your public key can only be decrypted using your private key. For more information on public-key cryptography, refer to http://en.wikipedia.org/wiki/Public-key_ cryptography.